Turnkey Third-Party Risk Assessment Services for Secure Partnerships
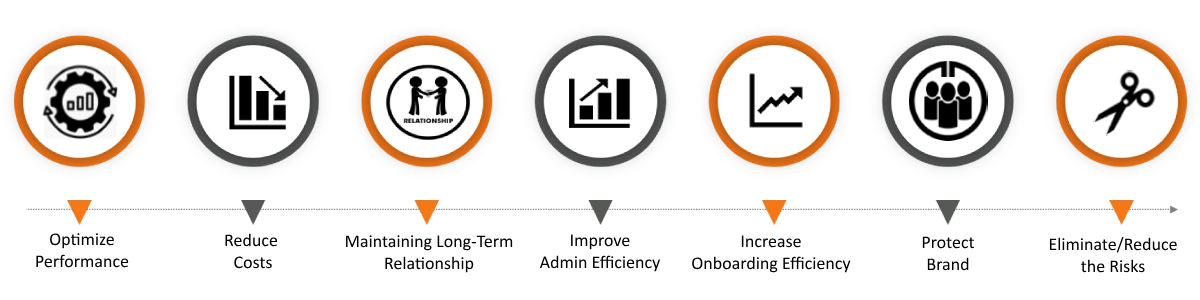
Third-Party Risk Assessment (TPRM) is a crucial process undertaken by organizations to evaluate and manage potential risks associated with their relationships with external vendors, suppliers, service providers, and partners. Since third-party entities often access an organization’s sensitive data and systems, assessing their security posture and compliance with industry standards is essential to safeguard the organization’s assets and reputation. The goal of a third-party risk assessment is to minimize potential security and compliance risks arising from interactions with external entities. It helps organizations make informed decisions about their business partnerships and ensure that their vendors uphold robust security practices and data protection standards. Here are the key services provided by third-party risk assessment by Shieldbyte Infosec:
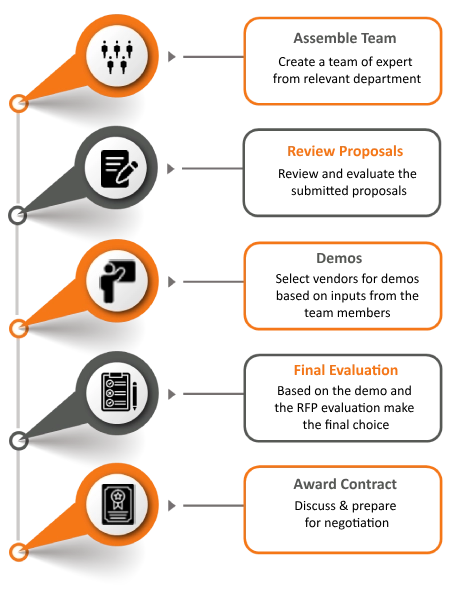
Vendor Identification
The first step is identifying all third-party vendors and partners with whom the organization / company / institution shares the important data or relies for critical services.
Gathering Information
The organization collects relevant information from vendors, including security policies, certifications, audit reports, and other compliance-related documentation.
Risk Categorization
The organization categorizes vendors based on their risk level. High-risk vendors, such as those with access to sensitive data or critical systems, will receive more in-depth assessments.
Contractual Agreements
The organization may include specific security requirements in the contracts with third-party vendors to ensure their commitment to maintaining a certain level of security.
TPRM
Services
TPRM
Services
Security Questionnaires
Vendors may be required to fill out security questionnaires that cover various aspects of their security practices, such as data protection measures and access controls.
Reporting and Documentation
A comprehensive report is generated, documenting the risk assessment results, any remediation efforts, and ongoing monitoring plans.
On-site Assessments (if needed)
For high-risk vendors, the organization may conduct on-site visits to assess the vendor's physical security measures and practices.
Risk Analysis
The collected information is analyzed to identify potential vulnerabilities and weaknesses in the vendor's security practices.
Risk Mitigation and Remediation
Based on the assessment findings, the organization works with the vendors to address identified risks and implement necessary security improvements.
Ongoing Monitoring
The risk assessment process is not a one-time event. Organizations need to monitor vendors' security practices and compliance over time continuously.