Security Assessment and Penetration Testing
Threat Modelling
Threat Modeling is a structured approach to identifying, evaluating, and mitigating potential security threats and risks in software applications, systems, or processes. It involves systematically analyzing and understanding the various components of a system, the interactions between them, and the potential vulnerabilities that malicious actors could exploit. Threat modeling aims to proactively design and implement security measures that reduce the likelihood and impact of potential threats.
Threat modeling is a fundamental practice in building secure software and systems. It fosters a proactive and systematic approach to security, enabling organizations to make informed decisions about security measures and prioritize efforts to protect their assets and users.
Threat Modeling
Services
Threat Modeling
Services
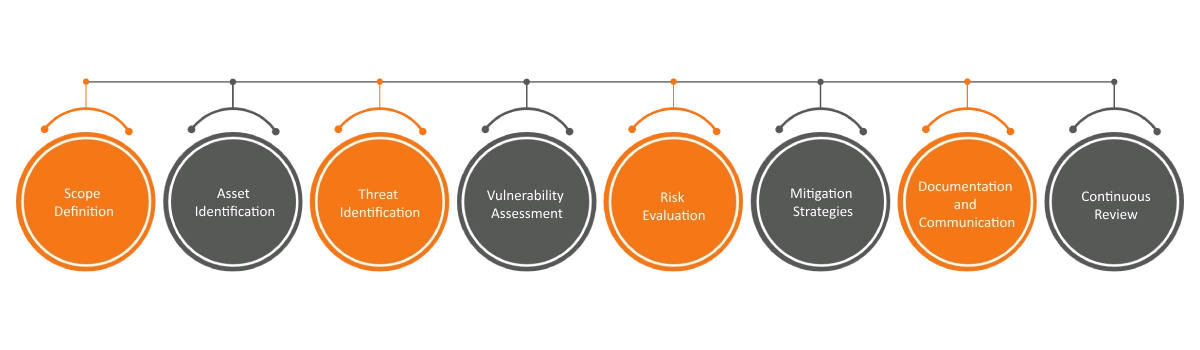
Scope Definition
Identify the system application focusing on threat modeling for defined scope boundaries, components, and interfaces that will be considered in the analysis.
Threat Identification
Identify potential threats that could exploit vulnerabilities and compromise the system's security. This includes considering different attack vectors and scenarios.
Vulnerability Assessment
Identify vulnerabilities in the system for threats that could be exploited. This involves analyzing potential entry points, weaknesses in code or design, and misconfigurations.
Risk Evaluation
Assess the potential impact and likelihood of each identified threat exploiting a vulnerability. Prioritize threats based on their potential impact and the likelihood of occurrence.
Mitigation Strategies
Develop and implement mitigation strategies to address identified risks. These strategies could involve security controls, design changes, code improvements, or process enhancements.
Documentation and Communication
Comprehensive threat model report with components, assets, identified threats, vulnerabilities, and mitigation measures with communication of actions to stakeholders.
Asset Identification
Identify and classify the assets or resources that need protection, such as sensitive data, user credentials, or critical functionalities.
Continuous Review
Regularly review and update the threat model as the system evolves, new threats emerge, or changes are made to the application.