Security Assessment and Penetration Testing
Vulnerability Assessment
Vulnerability Assessment is a systematic process by Shieldbyte infosec that covers identifying, analyzing, and evaluating security vulnerabilities in computer systems, networks, applications, and other IT assets. The primary goal of vulnerability assessment is proactively discovering weaknesses that malicious actors could exploit and recommending appropriate remediation or mitigation strategies.
Shieldbyte Infosec organizations proactively facilitate organization for vulnerability assessment, but it should be complemented by other security measures such as penetration testing, security awareness training, and incident response planning.
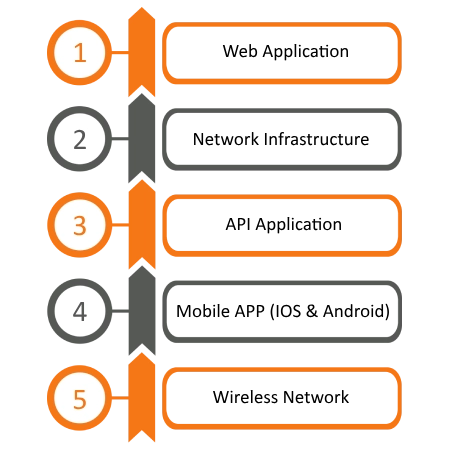
Vulnerability Assessment
Services
Vulnerability Assessment
Services
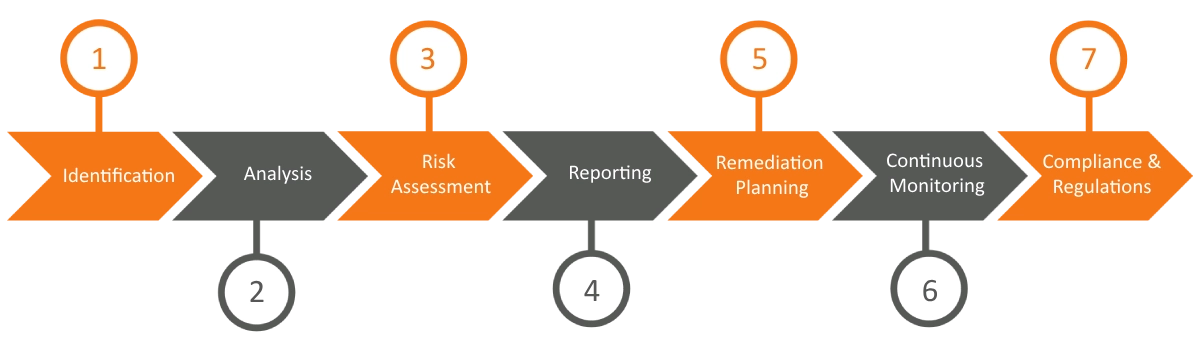
Identification
Identification involves discovering potential vulnerabilities in the system pertaining to software flaws, misconfigurations, weak passwords, and security weaknesses.
Analysis
After identifying vulnerabilities, they are analyzed to understand their potential impact and associated risks. This step helps prioritize which vulnerabilities need immediate attention.
Risk Assessment
Vulnerabilities are assessed for their potential impact on the organization's operations, data, and assets, assessing the significant threat and requiring mitigation.
Reporting
A comprehensive report outlines the identified vulnerabilities, their severity levels, and recommended actions to address them, covering crucial information security.
Remediation Planning
Mitigate the identified vulnerabilities based on the assessment report involving patching software, updating configurations, and implementing security measures.
Continuous Monitoring
Vulnerability assessment is an ongoing process, as new vulnerabilities emerge over time due to software updates, changes in the threat landscape, or other factors.
Compliance and Regulations
Vulnerability assessment plays a role in ensuring compliance with industry standards and regulations to meet regulatory requirements and demonstrate security.