Blogs
The only Source of Knowledge is Experience
Our experts love to share knowledge. And it shows! Whether you have a business or technology need, you've come to the right place to find information you can use.

11th June, 2025
Why SOC 2 Compliance Matters for Modern Enterprises
SOC 2 compliance is a widely recognized standard that helps companies manage data securely....

4th June, 2025
How VAPT Testing Protects Your Business from Emerging Cyber Threats
As businesses increasingly rely on technology, they face a rising wave of cyber threats....
28th May, 2025
GDPR Training: A Regulatory Necessity
The General Data Protection Regulation (GDPR) has fundamentally reshaped how organizations...
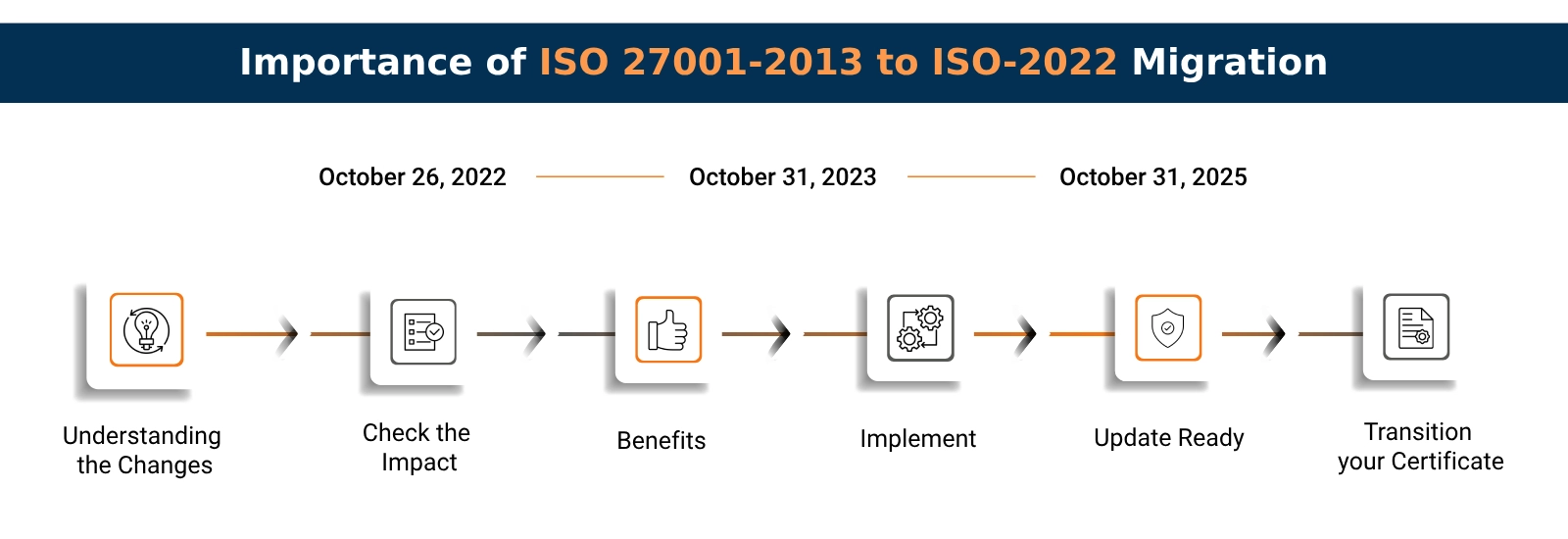
21st May, 2025
Importance of ISO 27001-2013 to ISO-2022 Migration
In the ever-evolving landscape of cybersecurity, the need for organizations to adapt to new...

14th May, 2025
Global Phishing Breach Trends: Understanding the Growing Threat
Phishing attacks have become a persistent and evolving threat in the global cybersecurity...

07th May, 2025
Understanding GDPR Breach Reporting: A Guide for Organizations
In the digital age, data breaches have become an unfortunate reality for many...

30th April, 2025
How to effectively achieve SOC 2 compliance
Understanding various criteria is the first step toward SOC 2 compliance. Your organization...

23rd April, 2025
Challenges in Data Privacy Compliance Due to AI
In today’s digital age, Artificial Intelligence (AI) is revolutionizing industries by...

16th April, 2025
The Revolutionizing Corporate Training: The Power of Built-In LMS Training Programs
In an era where the pace of technological advancement and market evolution is faster than...

08th April, 2025
The Critical Role of Vulnerability Assessment in Web Applications and SaaS Platforms
In the digital age, where businesses and consumers alike rely heavily on web applications...

02nd April, 2025
Securing the Digital Frontier: The Imperative of Cybersecurity Audits
As our world becomes increasingly interconnected through digital technologies, the stakes...

27th March, 2025
The Silent Threat: How 90% of Data Breaches Start with Phishing ?
In the digital age, cybersecurity threats loom larger than ever, with phishing emerging as...

20th March, 2025
Digital Personal Data Protection Act – 2023
In an increasingly digitized world, the protection of personal data has become a paramount...

13th March, 2025
Importance of VAPT in E-commerce Website
In today’s digital age, where online shopping has become an integral part of our...

06th March, 2025
Cybersecurity Threats Post-Pandemic: Safeguarding a Digitally Transformed World
The COVID-19 pandemic brought about a rapid and unprecedented digital transformation,...

28th February, 2025
RBI Cyber Security and Resilience Audit
The Reserve Bank of India (RBI), as the central banking institution of India, plays a...

21st February, 2025
Mitigating Post-Pandemic Cybersecurity Threats
The post-pandemic era presents both opportunities and challenges in the digital realm. As...
