Advanced Phishing Training and Simulation Services for Robust Cybersecurity
Why Phishing Training and Simulation Matter:
Phishing is a leading cause of data breaches, costing companies millions in lost revenue, regulatory fines, and reputational damage. Shieldbyte Infosec’s phishing training and simulation services proactively combat phishing attacks by educating employees on identifying phishing emails, malicious links, and other social engineering tactics.
Why Shieldbyte Infosec?
Expertise
Leverage our deep expertise in cybersecurity to stay ahead of evolving phishing threats and strengthen your defenses.

Proven Results
Our clients have seen measurable improvements in employee awareness and reductions in successful phishing attacks.
Dedicated Support
Our team provides ongoing support to help you maintain and improve your organization’s security posture.
Training & Simulation
Features
Training & Simulation
Interactive Training Modules
Engaging and interactive training modules that educate employees on recognizing and responding to phishing threats, tailored to various skill levels and roles.
Real-World Phishing Simulations
Simulate real-world phishing attacks, including spear-phishing and business email compromise (BEC), to test employee awareness and response in a controlled environment.
Customizable Scenarios
Custom scenarios reflect your organization’s unique threat landscape, ensuring relevance and effectiveness.
Detailed Analytics & Reporting
Comprehensive reports provide insights into employee performance, highlighting strengths and identifying improvement areas.
Instant Feedback & Learning
Employees receive immediate feedback when interacting with simulated phishing emails, turning mistakes into learning moments.
Key Benefits
Reduce Cyber Risks
Enhance Compliance
Detailed Analytics
Strengthen Incident Response
Boost Employee Confidence
Comprehensive Feedback
Reduce Cyber Risks
Enhance Compliance
Boost Employee Confidence
Strengthen Incident Response
Detailed Analytics
Comprehensive Feedback
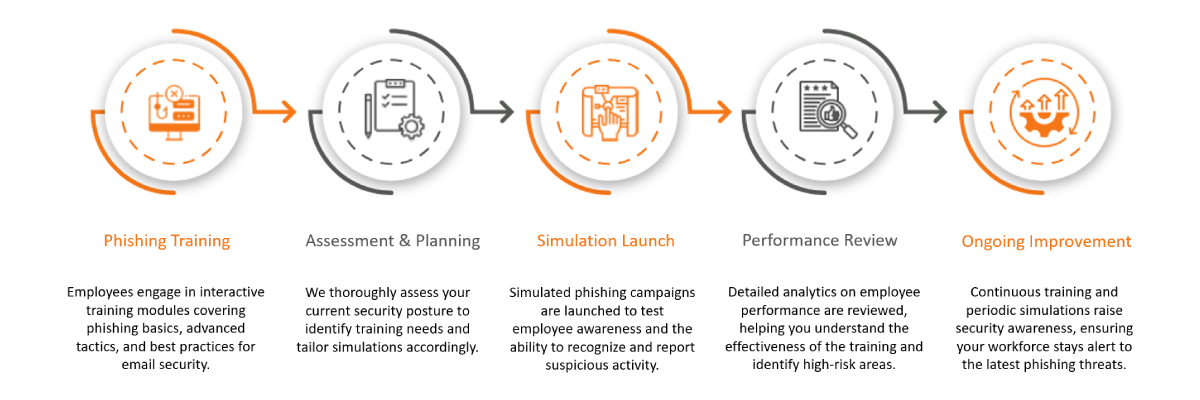
How It Works
Phishing Training
Assessment and Planning
Simulation Launch
Performance Review